 I have uploaded a 5 GB ISO file containing a new KTOWN variant of Slackware Live. This is the KDE Plasma6 Alpha release. Play around with it and perhaps you will be able to contribute to an improved Beta by finding and reporting the bugs you encounter.
I have uploaded a 5 GB ISO file containing a new KTOWN variant of Slackware Live. This is the KDE Plasma6 Alpha release. Play around with it and perhaps you will be able to contribute to an improved Beta by finding and reporting the bugs you encounter.
Get the ISO from my NL or my US server (US ISO still uploading at the moment). There’s also an MD5 checksum and a GPG signature file in those same locations if you want to validate the download.
A lot of packages did not compile yet for various reasons. I am not too concerned about that, next update hopefully will be more complete. A lot of work still needs to be done however (by the KDE developers) to port the remainder of KDE Gear (formerly called Applications or Software Collection) to Qt6.
Not ported to Qt6 as of yet are: artikulate cantor cervisia juk kamoso kde-dev-utils kdenlive kdesdk-thumbnailers kdev-php kdev-python kdevelop kget kgpg kig kio-gdrive kipi-plugins kiten kmix konversation kqtquickcharts krfb ktorrent ktouch kwave libkipi lokalize marble okular parley poxml rocs umbrello.
Still, I was impressed with the fully working and stable Plasma6 Wayland session when I tested an unreleased KTOWN Live ISO a week ago. Of course, as things go, I seem to have broken the Wayland session in this public release of the KTOWN Live.
The version of SDDM graphical session manager should also be Wayland-capable but I will test that in a future ISO.
Let me know in the comments section below what you think of this Alpha release.
![]() News about my chromium package (also its ungoogled sibling).
News about my chromium package (also its ungoogled sibling).
I was finally able to get the HEVC video and AC3 audio codec support working. There’s a patch set on github, maintained by StaZhu but I did not like the complexity and I am not really interested in GPU hardware-only support. The browser’s internal ffmpeg libraries playback HEVC just fine, taxing your CPU a bit more than in the case of a supported GPU.
Now, the Thorium Browser is also Chromium based and its developer Alex313031 used StaZhu’s patches and wrote some of his own to add not just HEVC video but also AC3 playback support.
Again, I did not like the complexity of his solution (documented on github) but could not get around using some of the patches provided by both. I simplified some of the others into a bunch of ‘sed’ commands. And that made it work for me.
The browser will now playback HEVC and AC3 media formats, as long as the container file is a MP4. I have not found how I can convince Chromium to also support MKV containers.
The chromium-119.0.6045.123 package is already available in my repository, and chromium-ungoogled is still compiling (the ungoogled patch kit only became available earlier today).
You can test the new HEVC playback capability here: https://test-videos.co.uk/ if you select any MP4/HEVC sample (none of those have sound) or Thorium browser test page: https://thorium.rocks/misc/h265-tester.html (those have AC3 audio).
Have fun!
 Just a heads-up to you people who wondered when Alien BOB would pick up on the KDE Plasma bleeding edge again.
Just a heads-up to you people who wondered when Alien BOB would pick up on the KDE Plasma bleeding edge again.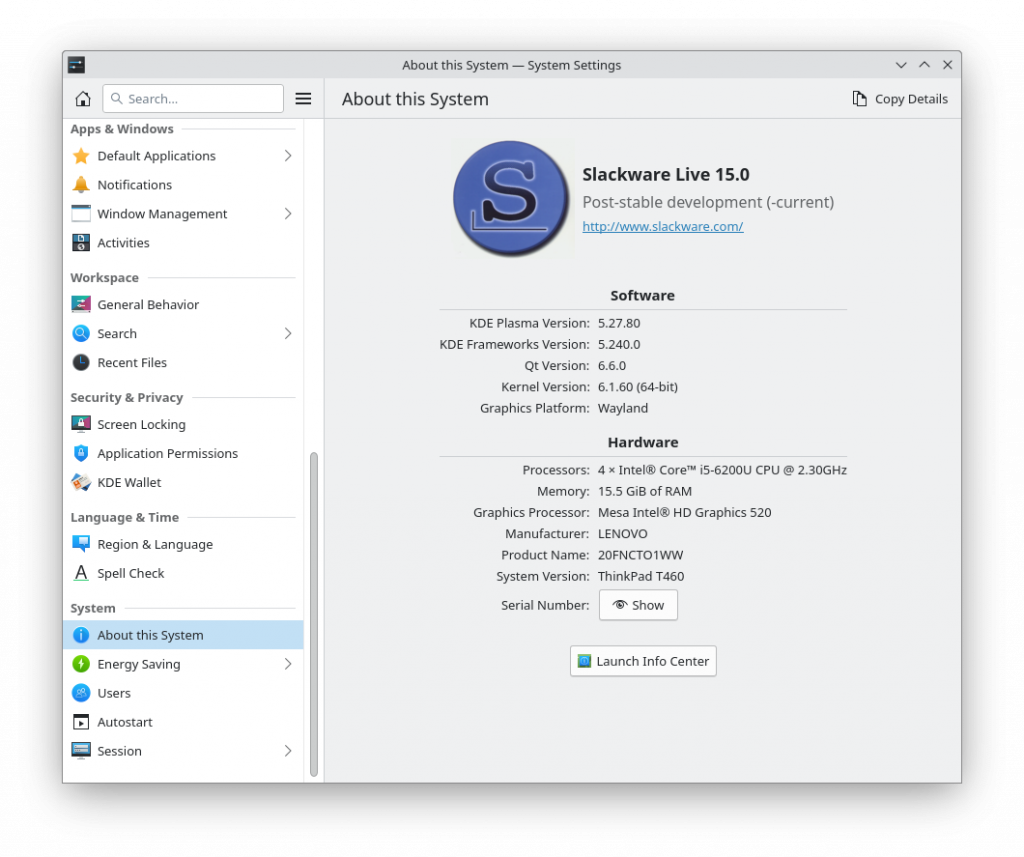
 I uploaded new 64bit packages for Chromium 118.0.5993.70 (also the un-googled variant) for which the
I uploaded new 64bit packages for Chromium 118.0.5993.70 (also the un-googled variant) for which the
Recent comments