Updates in liveslak
New ISO’s for Slackware Live Edition (based on liveslak-1.5.1) are available for download. You’ll find SLACKWARE (32bit/64bit), XFCE (32bit/64bit), DAW, LEAN, CINNAMON and MATE updated images (see below for download locations). I also refreshed the ‘bonus’ section with nvidia and broadcom-sta drivers matching the installed kernel, and other useful stuff.
All 32bit ISOs will boot a SMP kernel from now on, since the non-SMP kernels still refuse to execute the init script in the initramfs.
Firewall testers needed
This newest release of liveslak brings something that was recently discussed on linuxquestions.org. What about adding a basic firewall configuration to the freshly installed Slackware system? A new Slackware Linux computer may have several ports open already and some people are paranoid about any prying from the outside.
You will find as many firewall ideas as there are people in the discussion. So I based the core of the liveslak firewall on the code of Easy Firewall Generator of which I host a slightly modified version at http://www.slackware.com/~alien/efg/ . I added ipv6 support too. I know that this is old code, it’s also still using iptables instead of nftables but I wanted something functional that I knew well.
But in particular I want people to test the dialog-based configurator and give me feedback. You’ll notice that the configurator allows you to go back and forth in the various dialog windows. I also want to know what you think of the questions and the level of simplicity. Also look at the installed rc.firewall script. Does it do what you need it to do?
Also, does the resulting firewall configuration what you expected it to do? Is there anything that does not work?
Now, how does this firewall configurator work and where do I find it anyhow?
Every liveslak ISO since liveslak 1.5.1 has this functionality included. The firewall configurator will be invoked only when you use the (also included) setup2hd script to install the content of the Live ISO to your hard drive:
Adding a firewall is an optional step! You can choose to skip it during installation. The relevant files will be installed to your computer and you can call “myfwconf” at any time in future if you change your mind.
Note that this is a simple firewall. It does not do any NAT, it is meant for a single-homed single-purpose personal computer running Slackware which you want to protect from external attacks. The rc script will add a lot of sysctl tweaks to make your system safer, this is independent of opening (or not) any TCP or UDP ports via iptables.
Do I get this firewall when I use a Live ISO to install regular Slackware?
The firewall configurator is not available during installation of regular Slackware (i.e. from a HTTP/FTP mirror or a NFS/SMB network location).
If you would like to see the option of installing a firewall also for a regular Slackware installation, let me know. I am open to suggestions.
Some screenshots…
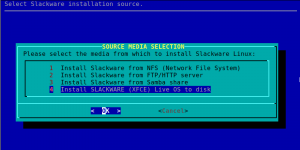
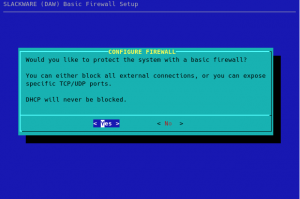
During the installation of the Live OS to your hard drive, the firewall dialog is inserted to the pkgtools setup directory so that it will be called during Slackware’s post-install configuration. The first question you will see when going through the configuration steps of your fresh installation is whether you want a firewall at all. You can opt out at this point, by selecting “No”, and no further questions will be asked:
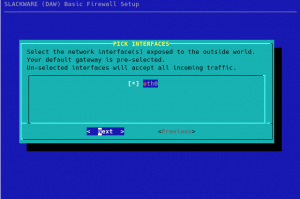
Next you will be asked to select the external network interface(s) that you want to have firewalled. Sometimes you’ll have more than one network interface (such as a laptop with its wired and wireless interfaces) which you want to protect with a firewall. This dialog will show you all detected interfaces and will have the one with the default gateway selected by default:
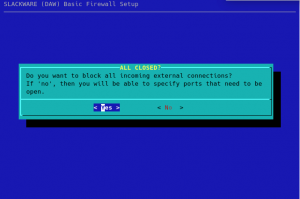
Next question to answer is whether you want a firewall to completely block all external connections (excluding DHCP traffic) or that you want to have specific ports open to the outside. Select “No” if you don’t want a completely blocking firewall:
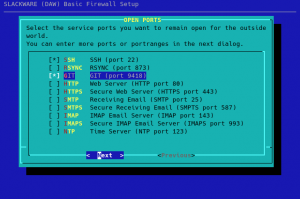
If you selected “No” in the previous dialog, you will be presented with a choice of common network protocols that you can open up from the outside by selecting them:
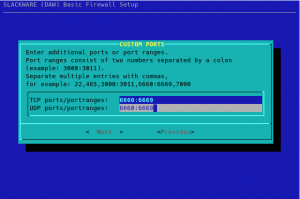
The next dialog allows you to specify additional TCP/UDP ports and/or port ranges to remain open:
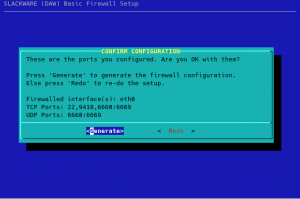
You will have a final opportunity to review the choices you made:
Pressing “Generate” will generate ‘ipv4’ and ‘ipv6’ configurations for iptables in the directory ‘/etc/firewall/’ and install the scripts “/etc/rc.d/rc.firewall”, “/usr/sbin/myfwconf” and “/var/lib/pkgtools/setup/setup.firewall”. The “myfwconf” script is the actual configurator shown in the screenshots. The “rc.firewall” script executes on boot and activates your firewall, whereas “setup.firewall” is a convenient script to be called from pkgtools:
Note that you can use the “Previous” button at any stage of the configuration to go to the previous dialog(s) and change your inputs. Pressing “Esc” at any time will bring you back to the very first dialog but then the default choice will become “No” instead of a “Yes”.
Download Slackware Live Edition
You can find a set of new ISOs based on liveslak on download.liveslak.org/latest/, the 64bit versions of them support Secure Boot.
Some people report that the ISO images won’t boot when copied (using ‘cp’ or ‘dd’ for instance) to a USB stick but they all boot properly if you use the ‘iso2usb.sh‘ script provided with liveslak to transfer the ISO content to a USB stick. Of course, this will give you nice persistent storage of all your modifications with optional data encryption, ideal for a secure on-the-road Slackware environment.
Get liveslak sources
The liveslak project is hosted in git. Its browsable cgit interface is here: https://git.liveslak.org/liveslak/
A set of the liveslak scripts can also be downloaded from http://www.slackware.com/~alien/liveslak/ or https://slackware.nl/people/alien/liveslak/
Remember Secure Boot
All 64bit ISOs are able to boot on a computer with SecureBoot enabled. You’ll need to enroll the liveslak public key (a SSL certificate in DER encoding format with the filename ‘liveslak.der‘) into such a computer during the very first boot. That certificate file can be found in the EFI partition inside the ISO image or on the USB stick you produced. It can also be downloaded from https://download.liveslak.org/secureboot/liveslak.der if you want. This DER certificate does not change when new ISO’s are released, so an updated ISO should boot normally on your SecureBoot-enabled system using the stored version of the ‘liveslak.der’ certificate which you enrolled in the past.
Cheers, Eric
Thanks, Eric! This is a great addition to Slackware.
Thanks Eric !
Time to update my liveslack ThumbDrive.
Merry Christmas / Happy Holidays !
— kjh
Hey, thanks for the new MinGW. Happy holidays!
This is great, thanks Eric for this and for the recent Chromium* updates as well.
Happy Holidays and a great 2022!
Thanks a gazillion!
I’ve dealt with your OCD.
Hello, some tweaks for you please:
1) due to latest sudo package, make_slackware_live.sh line 1879, change (ALL) to (ALL[^)]*)
2) perhaps add “uas” to the default KMODS, make_slackware_live.sh line 250, for initrd.img to support starting from more devices (eg drive to usb adapters and portable usb ssd)
3) make_slackware_live.sh line 2765, has qjackctl.desktop become org.rncbc.qjackctl.desktop ?
4) make_slackware_live.sh line 1296 also setting DEF_SL_REPO=”${SL_REPO}” seems to fix the -s option (the other way of SL_REPO= prefixing the command line is working fine)
Big thank you for everything you share with us.
The latest liveslak-1.5.1.5 deals with that sudoers change.
The ‘uas’ module is a good tip.
The desktop file for qjackctl is now called ‘org.rncbc.qjackctl.desktop’ and that’s something I need to address in the next liveslak release.
The implication of DEF_SL_REPO is something I need to think about, I need to check the logic of the script to see if it still makes sense.
Thanks for this feedback an any case! There will be a 1.5.2 release soon with these suggestions taken into account.
Hi! First, thank you Eric for this great work!
I am now using 1.5.0 mate from https://download.liveslak.org/1.5.0/ and have some doubts:
– The updated 1.5.1 is an update to shell script https://git.liveslak.org/liveslak/commit/?h=1.5.1&id=b727a6dd2e7776cfc7fac90bdb7ca0d9599e8db9 and does not have a folder for it?
– Should i maintain the system up to date with slackpkg pkgtools or it has another method ?
Note that Slackware Live and liveslak are not the same thing. Slackware Live Edition is the name of the ISO images, and liveslak is the project I maintain containing all the scripts to *generate* the ISOs.
The version of liveslak has no relation to the version of Slackware and MATE (or Cinnamon, …) that is used for the Live ISO.
I usually tag new versions of liveslak to accompany the release of a new set of Live ISO images, so that you can check in the repository what new functionality the new Live ISO has acquired. The boot screen of Slackware Live will always show you both the version number of Slackware and of liveslak.
If you want to update for instance your USB stick with a Slackware Live MATE on it, you have two choices:
(1) wait for the next update of Slackware Live MATE ISO and then use “iso2usb.sh -r” to refresh your USB stick with the latest release.
(2) update the Slackware OS on your Live MATE USB stick using slackpkg or upgradepkg.
With method (2) you can keep the Slackware on the USB stick up-to-date but you block the ability for a future refresh using “iso2usb.sh -r”. Methods (1) and (2) are incompatible ways to update your USB stick.
You might ask “when is that next release of Slackware Live MATE ISO” and I would tell you: when I have the time. These ISO refreshers are really low on my priority list since it is a time-consuming process to generate 6 ISO’s and also test them for proper functioning.
Just enjoy your Live OS on a stick and if you really want to keep up with -current, install Slackware to the harddrive of a computer.
Hello Eric,
thank you for your great job!
Just one thing… when Itry to mount an external ext4 partition with an administrator user different by the “live” one, the system owns the folder to “live” and I cannot access files… I’ve mounted my home partition (I’ve put the disk in an external USB adapter beacause my personal laptop is in mantenaince), but is mounted always with “live” user, not the one I’m logged with.
Is there a way to avoid this behaviour?
Thank you!
Mario
I think you can change the user/owner mount options in fstab?
man fstab
Hello Marco
I don’t use fstab for usb storage…