 Last week I told you about the change of theme which I applied to my personal blog. It seems that I was not done then.
Last week I told you about the change of theme which I applied to my personal blog. It seems that I was not done then.
On a different server I host the SlackDocs Wiki (https://docs.slackware.com/) and a lot more than that Wiki actually; docs.slackware.com is the same host which also provides you with the slackware.nl mirrors. This host is a physical server running in a datacenter on Slackware64 15.0 – nice and stable.
For an unrelated service I decided to upgrade the stock PHP 7.x to the 8.x version you can find in the ./extra directory because that is a version which offered better support and speed for that particular service.
Only the next day I found out that the PHP upgrade broke the Dokuwiki software which is what SlackDocs Wiki is actually based on. I could not use the Wiki’s admin interface to repair what got broken (afterwards I assumed I may have been thwarted by old cached PHP code; Dokuwiki obtains its rendering speed by caching the compiled PHP code so that it does not have to retrieve the script code all the time). Anyway, on the commandline I was able to upgrade the Dokuwiki to its latest version and along with that, all the plugins that I installed to extend the Wiki syntax or providing community editing capabilities.
So far so good, but the Wiki was still not rendering correctly with persistent errors in the browser and in the Apache httpd logs. They turned out to be caused by the Wiki theme (in Dokuwiki it is actually called a ‘template‘ not a ‘theme‘ like the blog). For SlackDocs I have been using the “MonoBook” template since its inception. The MonoBook template for Dokuwiki is inspired by the look and feel of the original MonoBook ‘skin‘ for MediaWiki (the wiki engine powering Wikipedia) which was replaced by the Vector skin in 2010.
This MonoBook template has not been updated since 2014 and is no longer supported by the latest Dokuwiki. Eventually I was able to fix the ‘bad code’ in the template and now the Wiki renders just fine using it.
But it got me thinking that it might be wise to switch to a supported theme. That sounds trivial, but I chose MonoBook for a reason: it supports Discussion pages. When you open a SlackDocs page, you will find a couple of tabs above the article, called “Article“, Discussion“, “Read“, “Edit“, “Old revisions” and “PDF export“. The Discussion tab allows anyone to comment on the actual article and thus hopefully spark a discussion – with the author or with other readers.
So I needed another template with that same Discussion capability. That was not so hard in the end; the same person responsible for the MonoBook template is also maintaining a Dokuwiki port of Mediawiki’s Vector skin. And even though it has not been updated either since 2014, Vector is fully supported by the latest Dokuwiki – no errors in its code.
I have ported the SlackDocs configuration for MonoBook to Vector and enabled it. The result can be seen on the current instance of SlackDocs Wiki. Most notable change is that the search entry field is now located at the top right of the page instead of halfway the left sidebar. Well, and it looks subtly different than MonoBook of course.
I hope you like it… but it’s not that I would go back to MonoBook if you don’t.
Enjoy! Eric
 A blog is something personal, and theming it just right is a challenge. You’ll surely have noticed that the theme of Alien Pastures has been changed overnight.
A blog is something personal, and theming it just right is a challenge. You’ll surely have noticed that the theme of Alien Pastures has been changed overnight. My work on the new Plasma6 for Slackware finally reached a level that I am OK with. I have uploaded a new KTOWN Live ISO image based on
My work on the new Plasma6 for Slackware finally reached a level that I am OK with. I have uploaded a new KTOWN Live ISO image based on 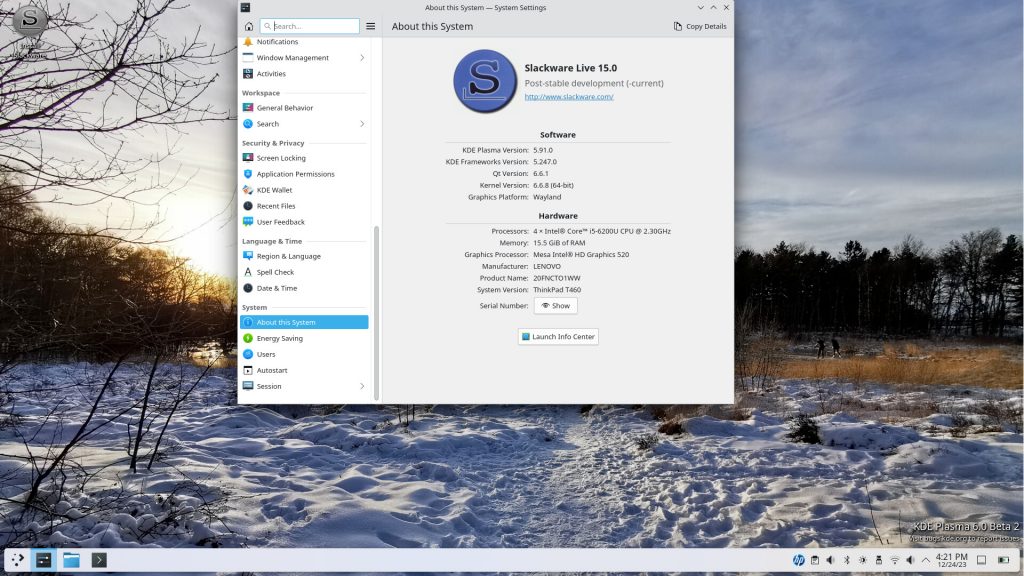
 Chromium 120.0.6099.129 for which the source code was
Chromium 120.0.6099.129 for which the source code was 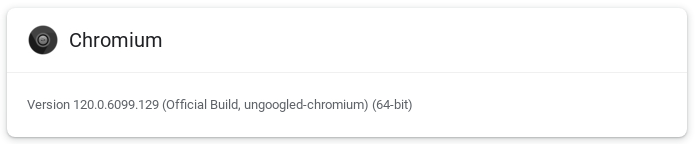
 Hi folks.
Hi folks.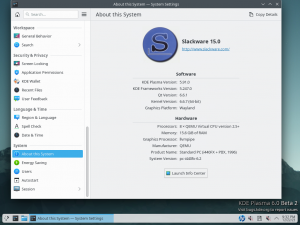
Recent comments