 Recently TrueCrypt has been in the news again, because of a couple of new critical security issues that were found for its Windows version. You can read more in these articles at Engadget, Threatpost and Extremetech. Windows computers with TrueCrypt installed can be taken over completely by a non-privileged user, and the computer does not even have to have mounted any TrueCrypt container.
Recently TrueCrypt has been in the news again, because of a couple of new critical security issues that were found for its Windows version. You can read more in these articles at Engadget, Threatpost and Extremetech. Windows computers with TrueCrypt installed can be taken over completely by a non-privileged user, and the computer does not even have to have mounted any TrueCrypt container.
These recently uncovered flaws were not found in last year’s code audit of TrueCrypt sources. Apparently this omission is due to the complexity of Windows drivers and “the kind of vulnerabilities that exist in many software on Windows and they are caused by lack of proper parameter validation in kernel mode code” according to Mounir Idrassi (VeraCrypt developer) in Threatpost.
Despite the fact that these new vulnerabilities are not affecting Linux, it is highly unwise to keep using TrueCrypt on Linux. The code is no longer maintained, it already has security issues and good alternatives exist.
The aforementioned VeraCrypt is a fork of the TrueCrypt code which is actively maintained, and the recent flaws found (to be disclosed next week) in TrueCrypt have already been patched in VeraCrypt 1.15 last weekend.
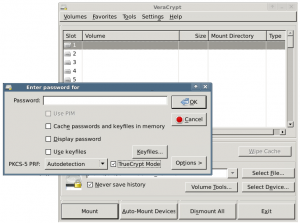
VeraCrypt is a drop-in replacement for TrueCrypt if you let it handle your encrypted container in “truecrypt mode”:
 I have built new packages for VeraCrypt 1.15, updating it from the previous 1.13 which I had in my repository. You can get the packages (for Slackware versions 13.37 and newer) here: http://www.slackware.com/~alien/slackbuilds/veracrypt/ or at its primary mirror location http://taper.alienbase.nl/mirrors/people/alien/slackbuilds/veracrypt/
I have built new packages for VeraCrypt 1.15, updating it from the previous 1.13 which I had in my repository. You can get the packages (for Slackware versions 13.37 and newer) here: http://www.slackware.com/~alien/slackbuilds/veracrypt/ or at its primary mirror location http://taper.alienbase.nl/mirrors/people/alien/slackbuilds/veracrypt/
Users of slackpkg+ merely have to run “slackpkg update && slackpkg upgrade veracrypt“, assuming that the repository mirror you are using is up to date.
Cheers! Eric
Many Thanks!
Man, sure you can read minds. Always thought veracrypt deserved a blog post. Many thanks !
Anyone here use BTRFS? Does VeraCrypt work with it?
Thank you Eric!
back in the days of truecrypt, in order to interact with btrfs it was necessary interact with the filesystem on the volume outside of TrueCrypt. something like
truecrypt –text –create –filesystem=none /dev/sdx1
truecrypt –text –mount –filesystem=none –keyfiles= –volume-type=normal –protect-hidden=no –slot=1 /dev/sdx1
mkfs.btrfs /dev/mapper/truecrypt1
mount /dev/mapper/truecrypt1 /mnt
to umount
umount /mnt
How do we do full-disk encryption with VeraCrypt on Linux? The documentation seems to imply that that’s only possible with VeraCrypt on Windows.
We don’t need veracrypt for full disk encryption in Slackware.
alienbob,
What’s the best way to do full disk encryption in Slackware?
thanks
Full disk encryption in Slackware (minus /boot) using LUKS is well-documented.
If you also want to encrypt /boot then you’ll need GRUB in a special configuration which supports LUKS volume decryption. Examples for such a GRUB configuration can be found on the Internet.
Just a friendly heads-up, VeraCrypt had been updated to 1.17.
Thanks.